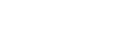unauthorized
英 [ʌnˈɔːθəraɪzd]
美 [ʌnˈɔːθəraɪzd]
adj. 未经许可(或批准)的
Collins.1 / BNC.21089 / COCA.10927
牛津词典
adj.
- 未经许可(或批准)的
without official permission- No access for unauthorized personnel.
未经允许不得入内。
- No access for unauthorized personnel.
柯林斯词典
- ADJ 未经授权的;未经许可的
If something isunauthorized, it has been produced or is happening without official permission.- ...a new unauthorized biography of the Russian President.
一本新的未经授权的俄罗斯总统传记 - ...the unauthorized use of a military vehicle...
未经许可使用军车 - It has also been made quite clear that the trip was unauthorised.
此行并未得到授权,这一点也已经说得相当明白了。
- ...a new unauthorized biography of the Russian President.
in BRIT, also use 英国英语亦用unauthorised
英英释义
adj
- not endowed with authority
- without official authorization
- an unauthorized strike
- wildcat work stoppage
双语例句
- Consul software tracks employee behavior and unauthorized access of company records.
领事软件铁轨雇员的行为和擅自获取的公司记录。 - Access Can an unauthorized user successfully access a control that only the administrators are authorized to use?
访问一个未经授权的用户能成功访问只有经过授权的管理员才能使用的控制权吗? - Sites should take reasonable steps to protect personal data from unauthorized access.
网站应采取合理的步骤保护个人资料,使其免受未经授权的取得和使用。 - It also has the security features to prevent unauthorized classes from retrieving personal information.
它还拥有阻止未授权类检索个人信息的安全特性。 - It involves constructing and analyzing protocols that prevent unauthorized access.
加密涉及到构造和分析用来防止未经授权访问的协议。 - Unauthorized use, or attempts to circumvent or bypass the security mechanisms of an information system or network.
非法使用,或试图回避或绕过信息系统或网络的安全机制。 - Specify a user name and password to prevent unauthorized access to the network resource.
指定用户名和密码以阻止匿名访问网络资源。 - Convention for the Protection of Producers of Phonograms Against Unauthorized Duplication of Their Phonograms, and Patent Cooperating Treaty.
《保护录音制品制作者防止未经许可复制其录音制品公约》和《专利合作条约》。 - This software can be used to prevent your email data from being stolen or damaged by unauthorized users.
它可以防止你的邮件数据被窃取或者遭到未授权用户的破坏。 - Incidents can include unauthorized access, malicious code ( such as viruses), network probes, and denial-of-service attacks.
事件可能包括未授权访问,恶意代码(如计算机病毒),网络探测,拒绝服务攻击。